零、选型
在开源PKI领域,主要有OpenCA、OpenXPKI和EJBCA。其中:
1、OpenCA已经在2016年停止更新;
2、OpenXPKI不支持OCSP及LDAP,能力不如EJBCA丰富;
3、EJBCA有商业版和社区版两个版本,功能比OpenXPKI多很多,尤其我们关注的OCSP及LDAP的支持;
一、EJBCA的部署
EJBCA依赖于EJB容器,部署较为麻烦,在其官网上没有给出docker部署方式,但确实有一个很新的官方docker在维护,地址为:https://hub.docker.com/r/primekey/ejbca-ce
根据该docker镜像中的描述,可以直接使用:
|
1 |
docker run -it --rm -p 80:8080 -p 443:8443 -h mycahostname -e TLS_SETUP_ENABLED="simple" primekey/ejbca-ce |
启动一个无需客户端证书的临时测试实例。或使用:
|
1 |
docker run -it --rm -p 80:8080 -p 443:8443 -h mycahostname primekey/ejbca-ce |
启动一个需要客户端证书的临时测试实例。
注意:
1、这两个命令中的mycahostname可更换为域名;
2、默认的80和443端口在很多地方是写死的,因此有条件的话可以考虑使用默认的80和443;
3、如果不使用TLS_SETUP_ENABLED=”simple”的环境变量,那么在容器启动后会给出客户端证书的下载地址和密码,如:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
[/opt/primekey/bin/start.sh] (process:1) [/opt/primekey/bin/start.sh] (process:1) Health check now reports application status at /ejbca/publicweb/healthcheck/ejbcahealth [/opt/primekey/bin/start.sh] (process:1) [/opt/primekey/bin/start.sh] (process:1) ************************************************************************************** [/opt/primekey/bin/start.sh] (process:1) * A fresh installation was detected and a ManagementCA was created for your initial * [/opt/primekey/bin/start.sh] (process:1) * administaration of the system. * [/opt/primekey/bin/start.sh] (process:1) * * [/opt/primekey/bin/start.sh] (process:1) * Initial SuperAdmin client certificate enrollment URL (adapt port to your mapping): * [/opt/primekey/bin/start.sh] (process:1) * * [/opt/primekey/bin/start.sh] (process:1) * URL: https://pki.example.com:443/ejbca/enrol/keystore.jsp [/opt/primekey/bin/start.sh] (process:1) * Username: superadmin * [/opt/primekey/bin/start.sh] (process:1) * Password: lyX5sy*********AcFsC * [/opt/primekey/bin/start.sh] (process:1) * * [/opt/primekey/bin/start.sh] (process:1) * Once the P12 is downloaded, use "lyX5sy***********AcFsC" to import it. * [/opt/primekey/bin/start.sh] (process:1) ************************************************************************************** [/opt/primekey/bin/start.sh] (process:1) |
默认情况下数据库使用的是容器内部的H2数据库,在真实场景下可以如下指定使用MySQL及持久化容器:
|
1 2 3 4 5 |
docker run -it -p 80:8080 -p 443:8443 -h pki.example.com \ -e "DATABASE_JDBC_URL=jdbc:mysql://mysql.example.com:3306/ejbca?characterEncoding=UTF-8" \ -e "DATABASE_USER=ejbca" \ -e "DATABASE_PASSWORD=YOUR_DB_PASSWORD" \ primekey/ejbca-ce |
容器启动成功后访问/ejbca/enrol/keystore.jsp,并使用提示的密码登陆、下载根证书、客户端证书,并在浏览器中导入客户端证书:
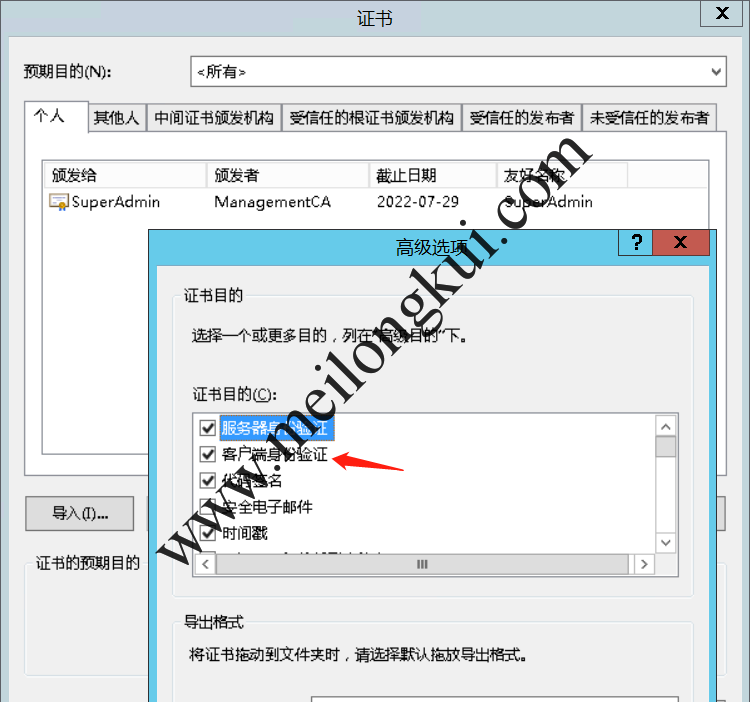
EJBCA的客户端证书
二、EJBCA的使用
EJBCA有几个关键地址:
1、Public Web,形如https://pki.example.com/ejbca,用户普通用户下载证书、CRL等;
2、Admin Web,形如https://pki.example.com/ejbca/adminweb,管理后台;
3、RA Web,形如https://pki.example.com/ejbca/ra,Register Authority,证书注册审批;
EJBCA Admin Web
EJBCA RA Web
EJBCA Public Web
三、EJBCA联动LDAP(发布证书到LDAP)
根据官网https://download.primekey.com/docs/EJBCA-Enterprise/6_12_0/LDAP_and_Publishers.html中的描述:
EJBCA has a modular support for Publishers. A publisher can be any external source where you want to send issued certificates and CRLs to be stored. The most common cases of Publishers, implemented by default in EJBCA, are Lightweight Directory Access Protocol (LDAP) directories and Active Directory (which is a special case of LDAP directory).
即当End Entity生成证书时会被发布到LDAP中。需要特别注意:
To publish in LDAP, you must create a Certificate profile in EJBCA that publishes to LDAP. If the publisher for LDAP is configured according to Configuring EJBCA above, there will be a section for Publishers available when creating/editing a certificate profile (with Edit Certificate Profiles).
Choose this, and then when adding end-entities, make sure they use the new certificate profile and voila, the certs will be published.
也就是需要在Certificate Profiles中配置Publisher:
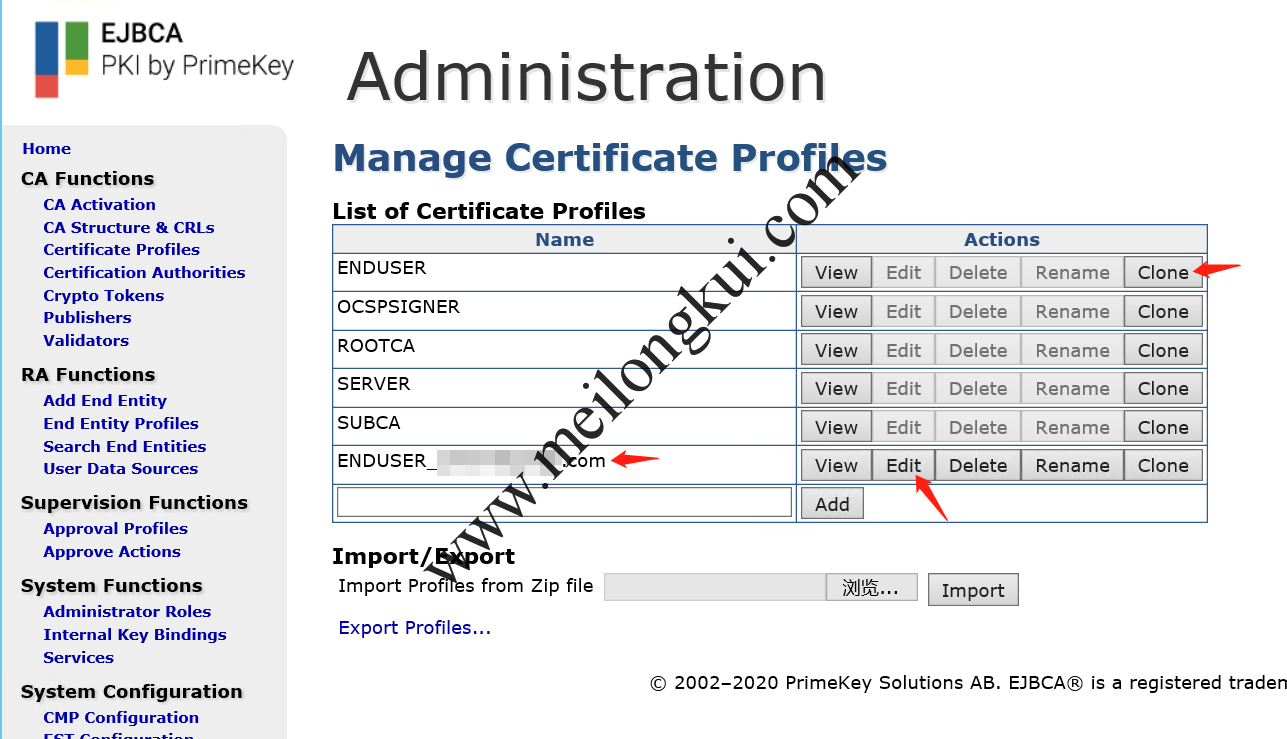
EJBCA Certificate Profiles-1
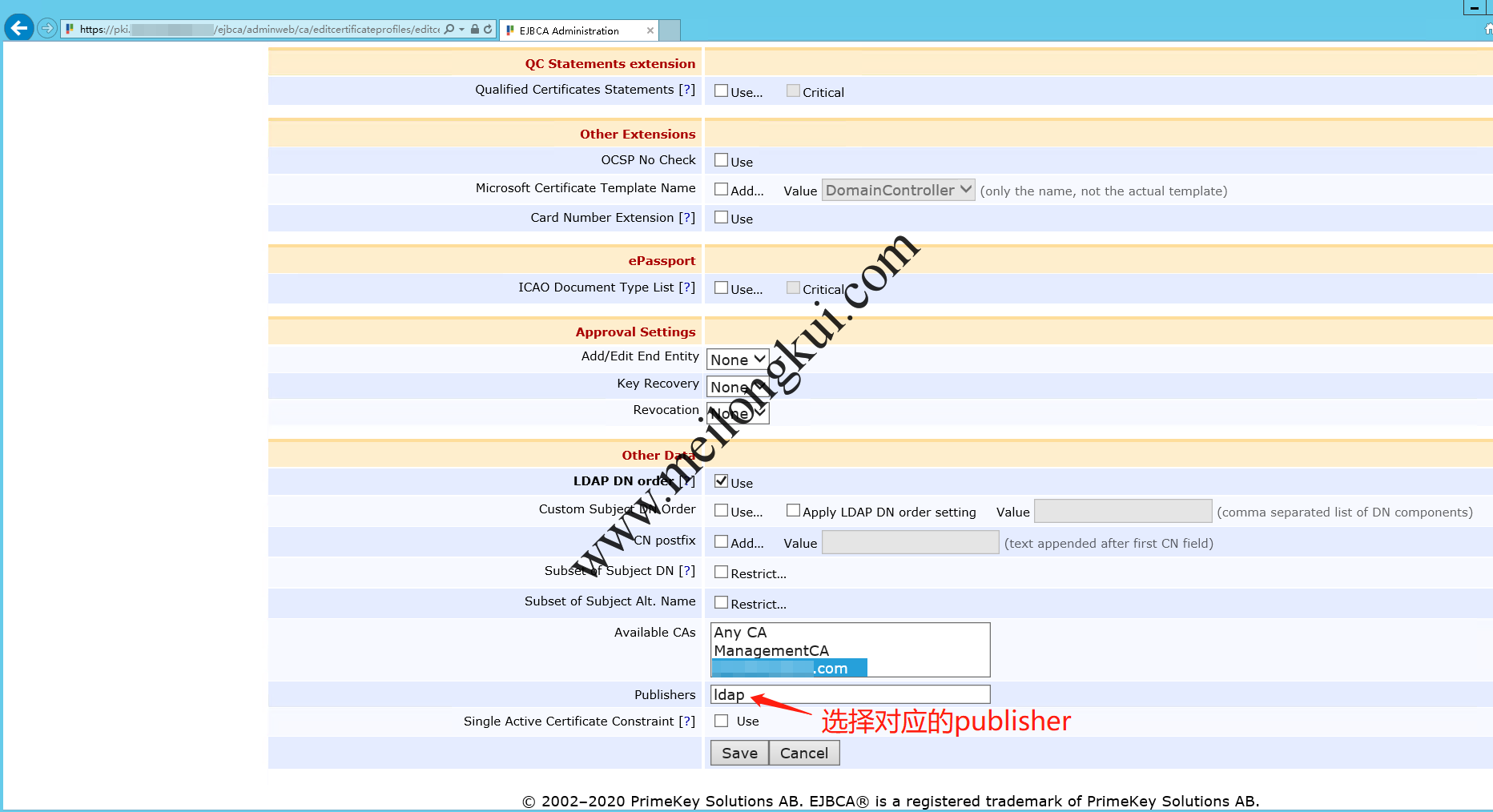
EJBCA Certificate Profiles-2
而Publisher为:
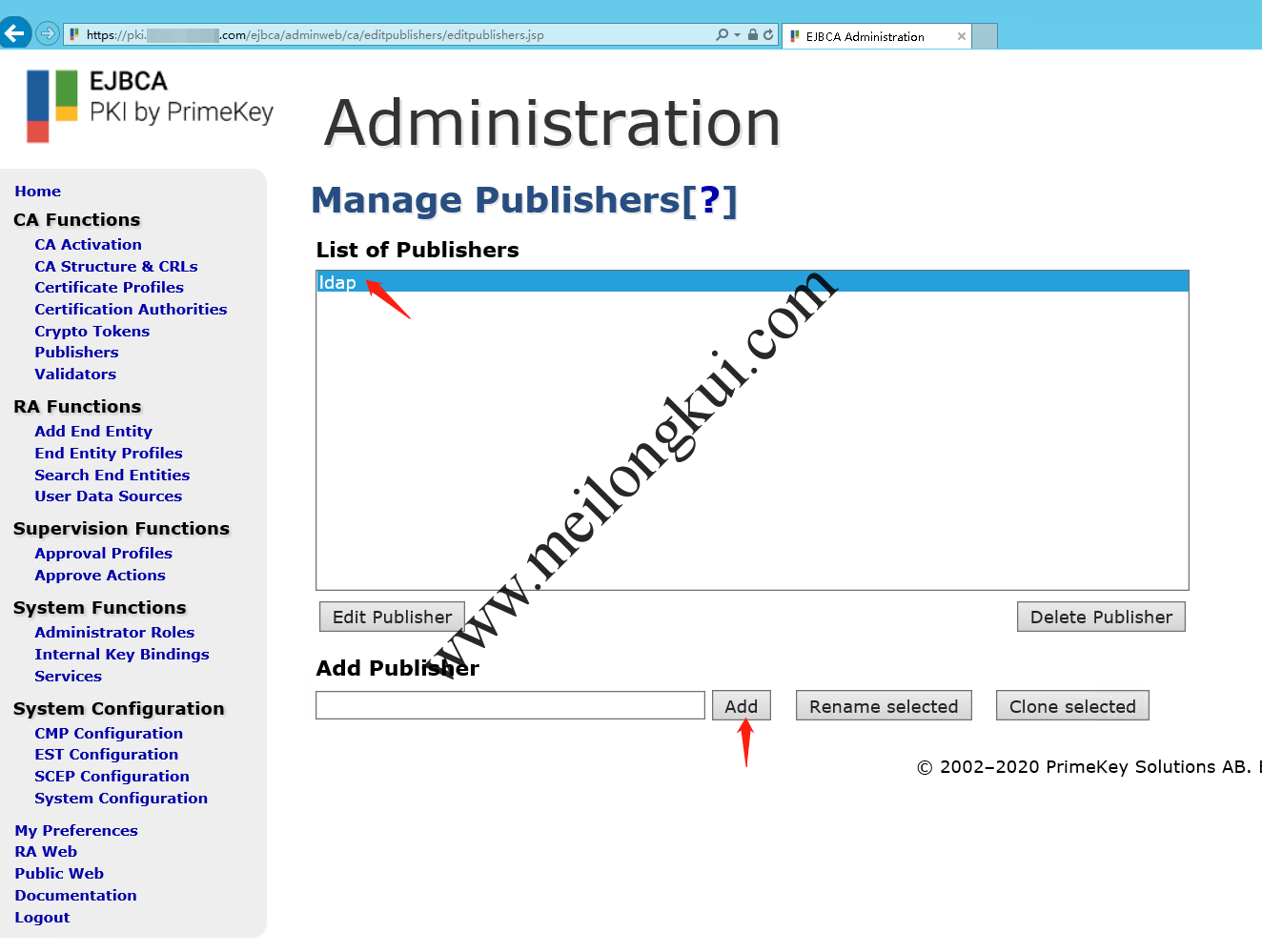
EJBCA Publishers
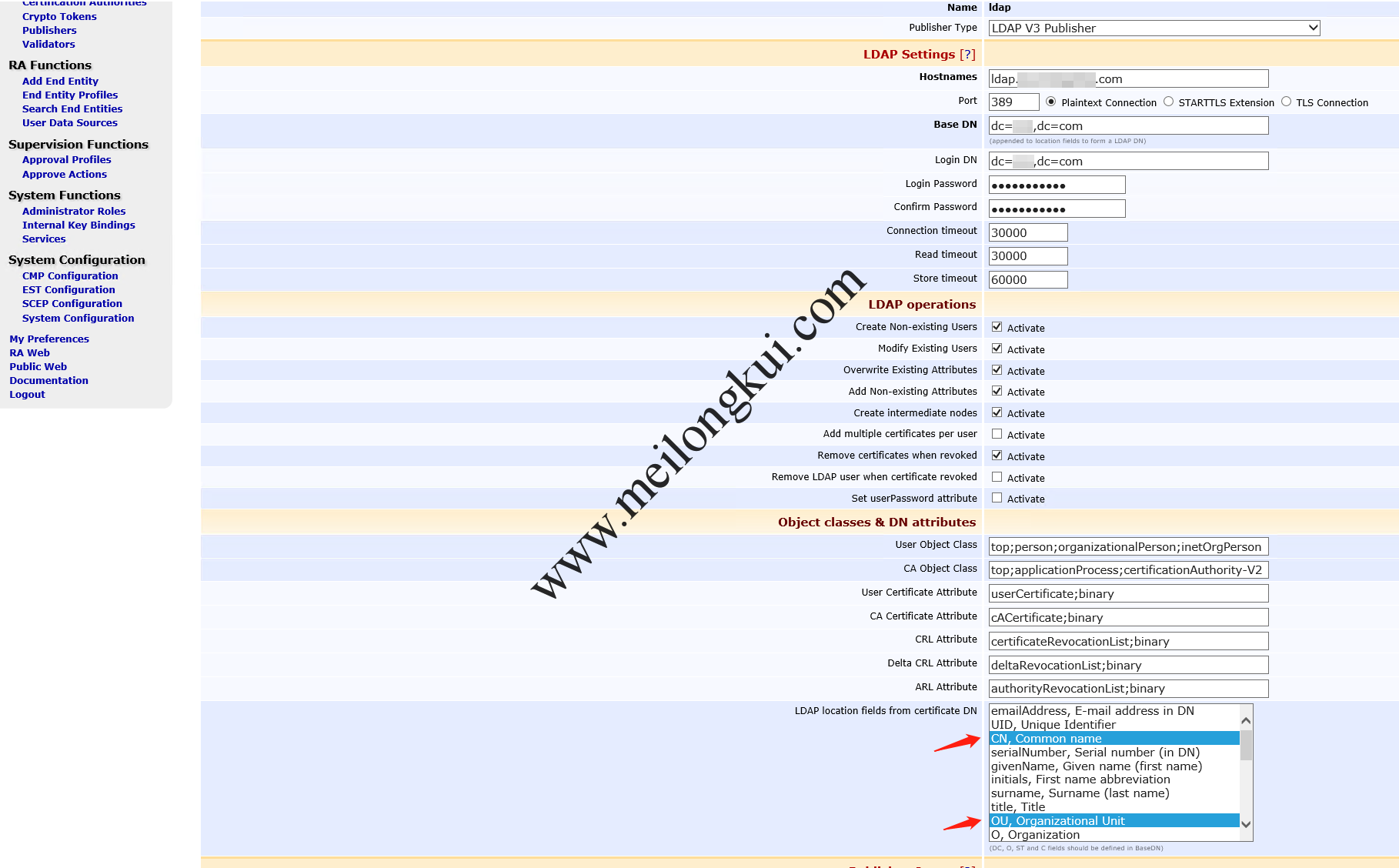
EJBCA Publishers-LDAP
注意其中DN的生成方式:
When EJCA creates an object to publish a certificate to LDAP it firsts builds the DN from the baseDN and ‘LDAP location fields for cert DN’. It checks if the entry exists in the ldap and either creates or modifies the entry.
Example: The certificate DN is “CN=Tomas Gustavsson,O=Foo,C=SE”, the BaseDN in the publisher is “DC=primekey,DC=se” and the CN is selected in “LDAP location fields from cert DN”. The resulting DN that EJBCA will search for in the LDAP and create if it does not already exist is “CN=Tomas Gustavsson,DC=primekey,DC=se”.
当证书GENERATED后,我们就可以看到LDAP中对应的数据了:
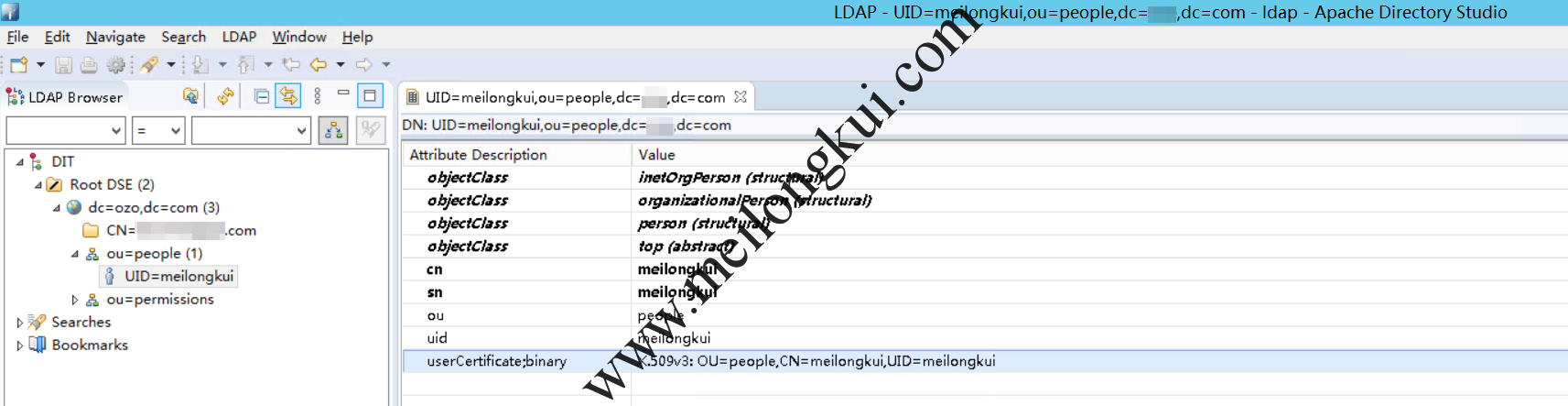
EJBCA证书创建后被发布到LDAP中
转载时请保留出处,违法转载追究到底:进城务工人员小梅 » EJBCA部署、使用并发布至LDAP
 进城务工人员小梅
进城务工人员小梅