As stated before, the CA utility will happily sign a request with any certificate, even if it is not a CA certificate.
以如下的证书链为例:
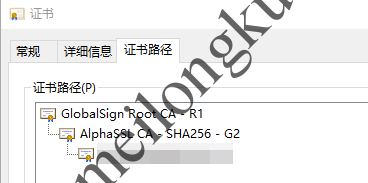
示例SSL证书链
RootCA:
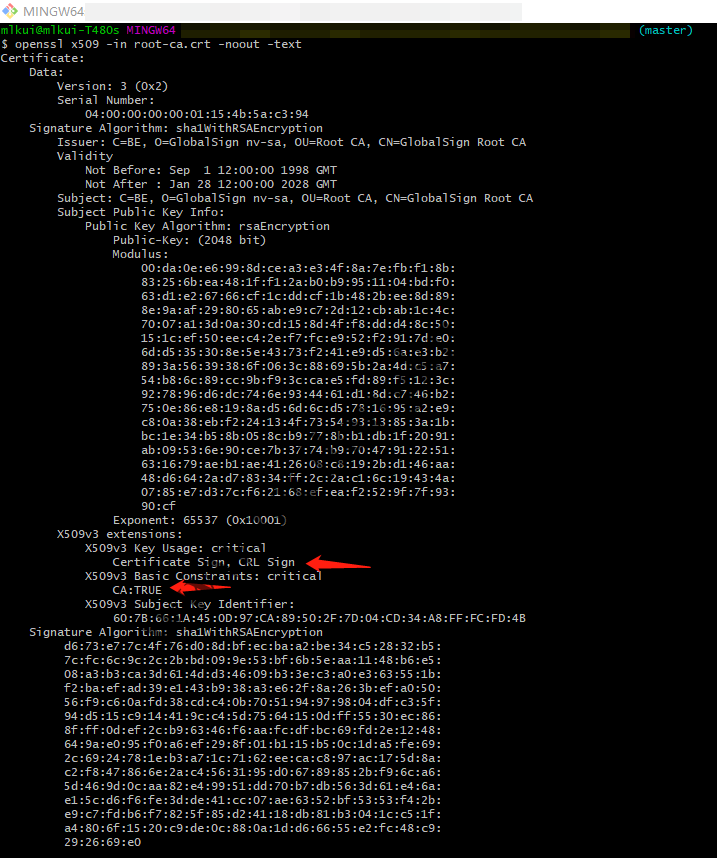
根证书
IntermediateCA:
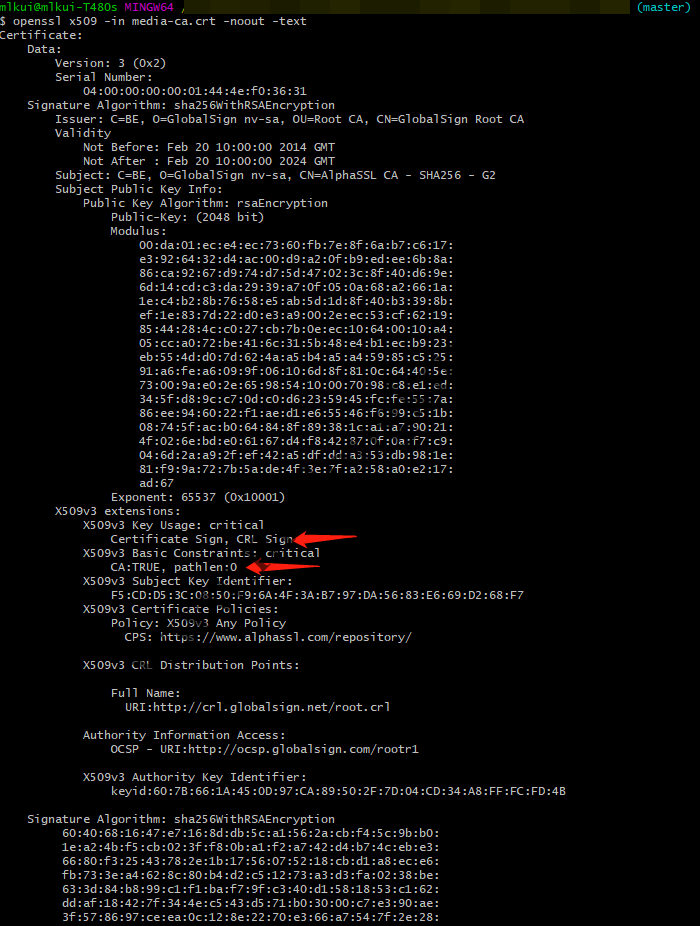
中间证书
SSL证书:
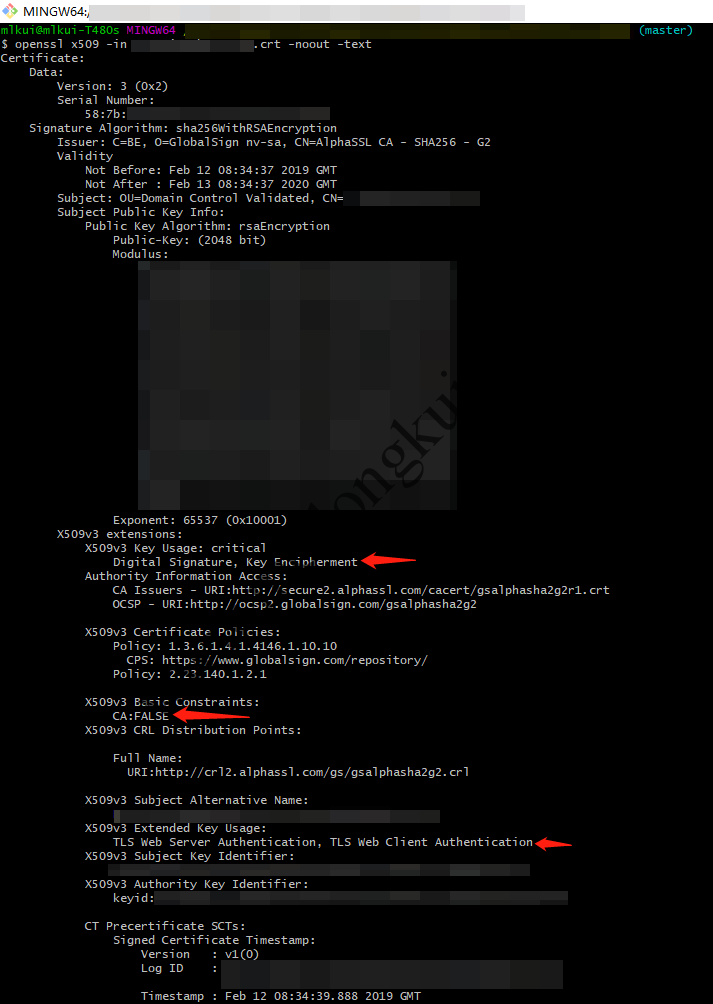
SSL证书
可见,SSL证书是:
|
1 2 |
X509v3 Basic Constraints: CA:FALSE |
即使其可以签出证书,得到的证书也是有问题的,无法通过证书链验证:
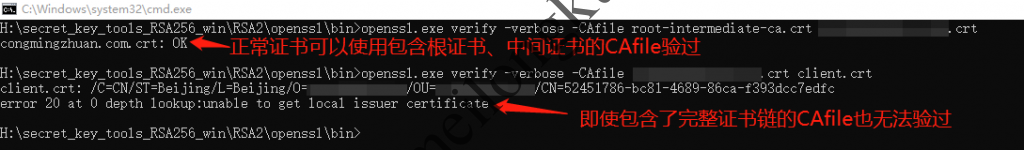
所签出的证书无法通过verify
查看PEM格式,发现签出的证书实际上包含了签发所用的SSL证书。但即使加上完整的证书链,在Windows中打开后也是诡异的:
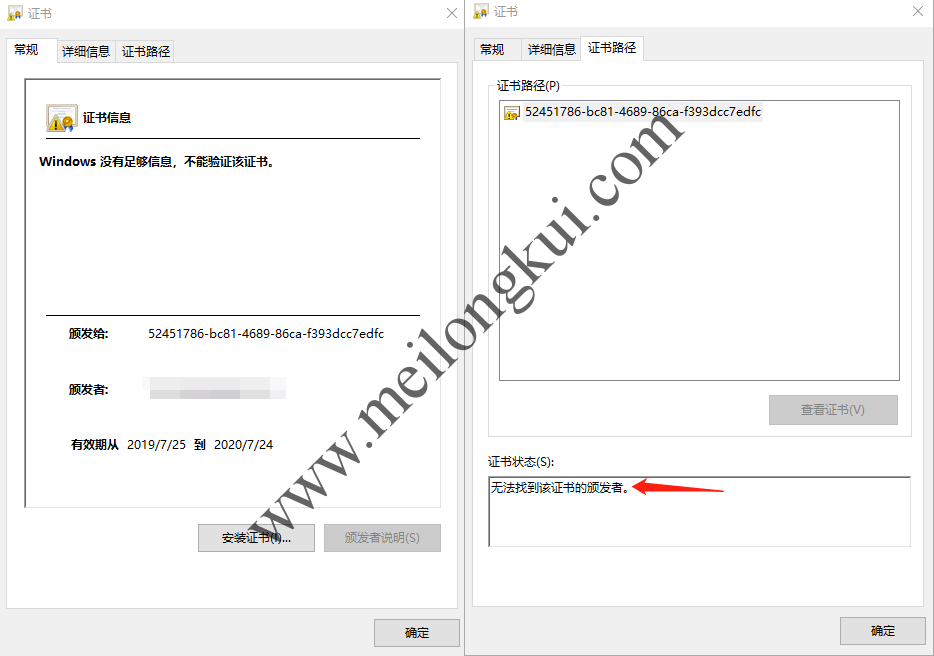
Windows认为证书无效
其显示“无法找到该证书的颁发者”。
参考资料:
1、https://superuser.com/questions/462295/openssl-ca-and-non-ca-certificate
2、http://techxperiment.blogspot.com/2016/10/create-version-3-x509-certificate.html
3、https://stackoverflow.com/questions/7230330/sign-csr-using-bouncy-castle/17281551
4、https://stackoverflow.com/questions/23736305/certificate-generated-through-csr-signing-with-bouncycastle-considered-untrusted
转载时请保留出处,违法转载追究到底:进城务工人员小梅 » CA utility will happily sign a request with any certificate, even if it is not a CA certificate
 进城务工人员小梅
进城务工人员小梅